High Security, Plausible Deniability and Two Factor Encryption: You're the Weak Link
Security is an illusion, especially with computers. The systems are so complex, handled by so many different people that nobody really has a good idea of how everything works. Even the best specialists have knowledge gaps: software, hardware, etc… This creates a security nightmare: breaking stuff is trivial, fixing the systems is nearly impossible.
High Security Systems Still Exist
There are systems that are protected against nearly all attacks. Their main philosophy is not to fix the security issues but to prevent an attacker from accessing the system in the first place. You can’t hack something that’s not there. However these systems are painful to use, especially for their lack of internet connection. Here are the main techniques used in a high security system:
-
Air Gapping: The device can’t connect to anything that is not physically plugged into it. No internet, wifi, bluetooth, speaker, microphone, webcam. Anything that can communicate with the outside world is physically removed from the electronic device.
-
Non Contamination Protocol: Air Gapping is not sufficient (stuxnet is a good example of why it isn’t). Everything plugged into the air gapped device (like usb keys) can’t be plugged anywhere else. No exceptions. This prevents any information from getting out. I would even recommend not to plug anything that comes from another device (stuff like stuxnet or ransomware can still make some damage).
-
Physical Protection: Non-contaminated air gapped devices are impossible to attack remotely. The only way is to access them physically. Having the electronic device hidden in a place that is difficult to access (e.g. in a safe) will protect it better.
-
Full Disk Encryption: Physical Protection is not foolproof. An attacker can still get access to it with enough resources. To protect the information inside your device, encrypt its entire content. Not all types of encryption are made equal, we will talk about it later in this article.
-
Tamper Evident System: The last remaining attack on an electronic device, after you’ve already used all of the above techniques, is to tamper it. The main goal is to access the encryption key when it is entered. Using tamper evident techniques (hardware and software) will alert you that somebody has modified your device to access your password (more about it in Two Layers of Encryption below).
-
Backup: The last remaining problem is system failure. As long as your backups follow all of the above techniques, you can have as many as you want. Store them in a different location for increased safety.
Security is more about how you use the hardware/software rather than having a secure device in itself. It’s more about protocol than technology.
I have seen classified environment with less security than the one just presented. Using a device with all of the above techniques will guarantee an electronic fortress. However this creates a big problem: you become the information’s weak link. It means that an attacker will no longer try to hack or decrypt your device, but instead will threaten you in order to access the information inside it.
Plausible Deniability
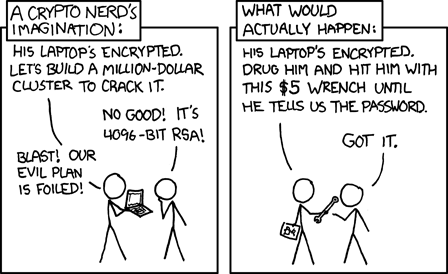 Rubber-hose cryptanalysis from xkcd
Rubber-hose cryptanalysis from xkcd
To prevent being compelled to reveal your passwords, somebody invented Deniable Encryption. Basically you have two passwords: when you enter the first one the information decrypted is different than when you enter the second one. You use your device with the second password to work on the sensitive information (which can’t be accessed using the first password). In case somebody threatens you, you give them the first password. They will decrypt your device and see that there is no information (or if there is, info that is not sensitive).
In practice Plausible Deniability is problematic:
-
Tools and techniques exist to detect the presence of a secondary password (Deniable Encryption).
-
If your attacker sees that the system can use plausible deniability, they may not believe that there is only one password and therefore may continue to threaten you until you reveal the second one.
-
It will be harder for you to pass lie detection tests since you are still able to access the sensitive information using a secondary password.
What you really want, if threatened, is not to be physically able to unlock your device. If you can’t decrypt the information, nobody has a reason to threaten you.
Two Factor Encryption
Two Factor Encryption uses your password in addition to something you possess to generate the encryption key of your device. In general these secondary factors look like USB keys. To decrypt the information, you need your password (50% of the key) and some information you don’t know, stored/calculated by your secondary factor (the other 50% of the key).
You can’t open your device without these two elements: your password and the secondary factor.
The beautiful thing is that if you break the secondary factor, you won’t be able to access your device and its backups. You can’t be compelled to decrypt the information, because you simply can’t: your password, which you can now freely communicate to your attacker, will not be enough.
Using Two Factor Encryption creates a physical “red button” which, if pressed, will destroy all access to the information in your devices (even offline backups stored in different locations).
This also has the side effect of preventing you from accessing your device’s information ever again. This is one disadvantage of Two Factor Encryption over Plausible Deniability, which is that you can’t access your data after the attacker is done with you. However if you’re handling sensitive information, it is very likely that you’d rather have it destroyed than letting it fall into the wrong hands.
YubiKey

A nice, affordable second factor for your encryption is a YubiKey. However there is no straightforward manual on how to use it, and the key has quite complex modes and functionalities.
If you are not a technical person, I will recommend using the password mode. It is not as safe as the challenge mode, but it will be simpler to use and to configure.
Password Mode
The YubiKey can act as a usb keyboard. When the button is pressed, it will send a combination of keys (a kind of password) as if someone was typing. This makes it compatible with everything that requires a typed password. However using this mode implies that the 50% of the key coming from your 2FE will be the same across all devices. If it is intercepted it will drastically reduce the security.
To use the password mode, when prompted to your login information, enter your password (the thing you know), then plug your YubiKey and press the button. It will “type” the rest of the “password” (the thing you possess but don’t know). You can then access your device.
In this scenario the thing you know is 50% of the password, the other 50% of it (which you don’t know) is stored on your YubiKey and typed for you when you press the button.
Challenge Mode
The challenge mode is safer than the password mode, however it is more complex to configure and use. The information received from the YubiKey (the 50% of the key that comes from the 2FE) is different for each device. If it is intercepted, it will not compromise the security of other devices.
To use the challenge mode, your encryption software has to be compatible with it (contrary to the password mode which works with everything). When prompted to your login information, enter your password, and then the software will send a challenge (a phrase or an id you pre-configured) to the YubiKey which will respond with the missing 50% of the encryption key. The combination of the two elements (your password and the 2FE response), creating the encryption key, will unlock your device.
The advantage of the challenge mode is that if you configure a different challenge (phrase or id) for each device you will have a different response each time, making your encryption key unique on all your devices and backups. This increases the security a lot in case one of them is compromised.
Not All Encryptions Are Made Equal
Cryptography may be the hardest thing in security. If you screw it up, nobody will come and tell you about it, and you will pay the consequences later on.
Serpent Encryption Algorithm
Serpent was part of the finalists of the AES competition. It was judged to be the most secure algorithm of them all, but was discarded due to its speed. However 20 years later, the computational power of everything exploded. Today the difference in speed between AES and Serpent doesn’t matter anymore, however the difference in security still does. This is part of the reason why you should use Serpent everywhere ;)
Truecrypt
Truecrypt is an awesome tool that has been proved to be complicated to break. The tool was suddenly discontinued in 2014 in what seemed to be due to third party pressure. An independent audit was financed by the community in 2013. The summary was released in 2015, showing “no evidence of deliberate backdoors, or any severe design flaws that will make the software insecure in most instances”.
Given that it’s complicated/impossible to break, that it’s been audited without any security flaw found, and the pressure put on the developers to stop the project: it’s safe to say that you should use it everywhere.
You can find Truecrypt here, the last version is 7.1a. Use the 3 ciphers cascade encryption mode.
If you use the hidden volume feature, be careful with older backup versions of your file container. The difference between the older version of the container and the newer version will reveal the use of an hidden volume (bytes will change where there is supposedly no data). Try to backup the content of your container inside a new one, so that there is no match at all between the backups and the original container.
Password
The last line of defense for your data is your password. Depending on the system you are using, the encryption key will be encrypted using your password, or directly derived from it. This means that even if you are using an unhackable electronic fortress, your security will drop to zero if you use a password like “1234”.
The short answer is to use a unique and long passphrase for each of your device/account. You can find more details on password safety in our podcast episode “Your Password Is Not That Safe”.
Two Layers of Encryption
A Tamper Evident System will warn you that your device has been modified to steal the encryption key (or your password). However most of them will not block the attack and will warn you once it’s already too late.
Practically speaking, having a Tamper Evident System will probably compromise your encryption key. That’s why you need 2 layers of encryption: the first one is a full disk encryption for the Tamper Evident System, the second one is a file container (like a Truecrypt container) for your data (unlocked once everything is notified as normal). From a user’s perspective it means entering two passwords instead of one.
In case of a breach, you will be notified by the system before entering the second password and therefore you will be able to stop before doing so. The attacker will be left with an encrypted file container (which if you use Truecrypt, has a better security than the full disk encryption). Your data will remain safe and inaccessible.
2FE Subtilities
Using Two Factor Encryption may be tricky. The security of the entire system relies on a small USB device and a password. Handled wrongly, it may have devastating consequences.
Train To Break It
Breaking the 2FE device may be difficult (YubiKeys are quite solid). When you will need to split the device in half, you may not have a lot of time. It may be a good idea to practice doing it with another device.
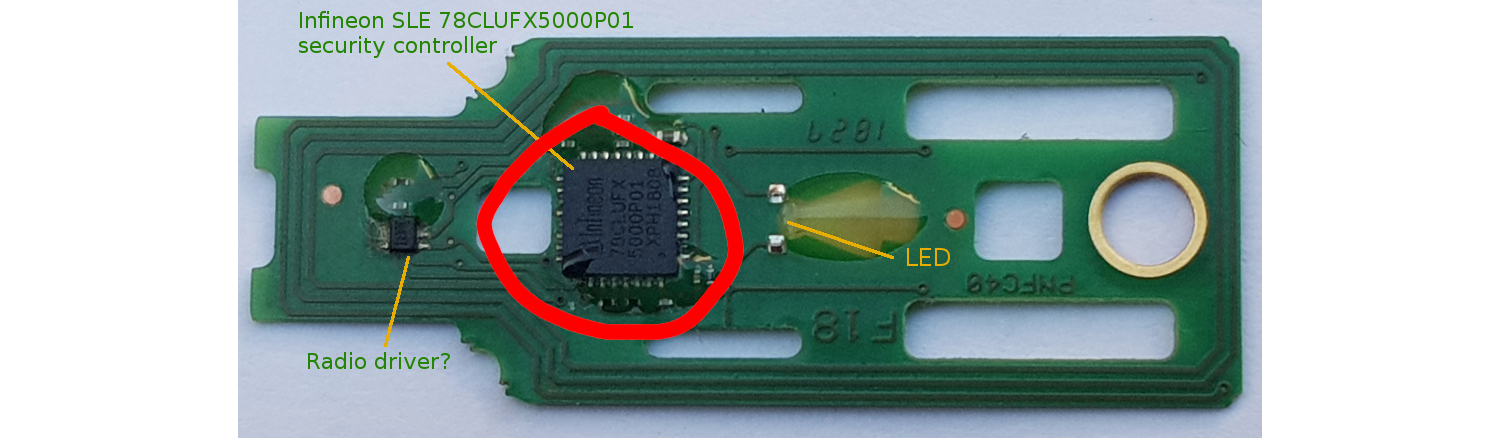 YubiKey Circuit from hexview.com
YubiKey Circuit from hexview.com
Depending on which model you have, you may need to break it at a different place. What you want is to snap the microchip containing the information. If the 2FE isn’t broken correctly, your attacker will still be able to access it.
Always On You
Always have the 2FE device on you. In case there’s a problem (e.g. kidnapping), you will have a small window of time to break it. Between the stress and adrenaline from a difficult event, it will be hard to focus. Train mentally to have the reflex to break the 2FE.
Don’t Back It Up
The entire security of the Two Factor Encryption resides in the single point of failure. If you backup your 2FE device, it will severely affect the security.
YubiKeys are quite reliable. However if you are afraid of a malfunction, you can have a duplicate as long as it follows the same rules. It means having your 2 devices always side by side. Take into consideration that in case there’s a problem, you will need to break two devices instead of one (this will take twice as long in a situation where time is crucial). Alternate their use to check regularly that both are in working condition.
Scripting
If your encryption system is not compatible with 2FE (like Truecrypt) you can always interface its use using a script. You can also use the password as a challenge for the 2FE, leaving less trail.
Bonus Points: Emails And Clouds
Although Two Factor Encryption doesn’t protect you from being hacked over the internet (that’s why we use air gapped devices), nonetheless it’s always a good idea to have it on your less secure devices. One cool thing about Two Factor Encryption is that it can be used with anything online that has end-to-end encryption (with password protected/derived keys).
2FE is not the same thing as OTP (Two Factor Authentication), which these services also offer. You should enable OTP everywhere, the YubiKey is compatible with it.
ProtonMail is an email provider that offers end-to-end encryption. Using 2FE with their service allows you to protect your email communications in case of threats to access your data.
Cloud
Tresorit and Mega are online cloud solutions for your files that offer end-to-end encryption. Using 2FE with them will protect your files from being accessed if you are being threatened.
If you install E2EE apps on your smartphones, be careful, as some may store the encryption keys on the phone. Securing a smartphone is a lot more difficult, these stored keys have more probability to be accessed by your attacker.